blog

Organizations do not operate in legal vacuum. Their actions or inactions, words and deeds carry legal responsibilities and consequences. With Cyber security issues popping up by the seconds and becoming increasingly very complex by the day, organization must be at the forefront of the efforts in the IT and Cyber security communities to address the issues. As a starting point, organizations must beef up their legal policies to guide their IT and Cyber security practices for effectiveness and not avoid or minimize legal liabilities.
Overview
Data is the most valuable asset and resources second to human that any organization must manage. Data management determines organizations profitability and survivability:
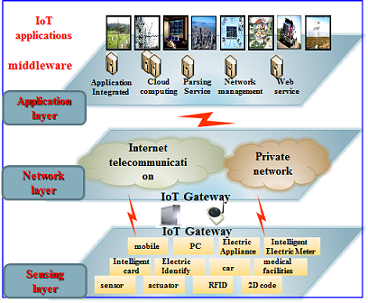
Every enterprise will be affected by the benefits and challenges that Internet of Things (IoT), the growing phenomenon by which not only people, but also “things” — vehicles, commercial and industrial equipment, medical devices, remote sensors in natural environments — are linked to networks that are connected to the internet. The profound impact on businesses and the business value it brings will to a large extent be dependent upon overcoming the overwhelming Cybersecurity challenges that characterize the phenomenon of connecting “Things” in the Internet.
The Attack. Equifax Hackers Stole 200k Credit Card Accounts in One Fell Swoop – Period! As widely reported on September 17, 2017, Visa and MasterCard have been sending confidential alerts to financial institutions across the United States this week, warning them about more than 200,000 credit cards that were stolen in the epic data breach announced last week at big-three credit bureau
Enterprise Risk Management (ERM) market are largely driven by the Finance & Banking (F&B) sector’s interpretation of what ERM means. Classical ERM takes traditional risk methodology in the areas of Credit, Market and Operational risk management and extended that out to other areas of their businesses and called that ERM. In actuality the F&B institution’s methodology for managing risk is applying too much emphasis on backward-looking analysis of loss, as opposed to a more forward-looking speculation about potential loss (or risk) in future.

It takes a hacker only one web page and one email to gain access to a major corporation’s internal network. Catchy we know, but this is not an exaggeration of what an attacker can do to gain access on their internal network. In culmination with exploiting a few systems on the internal network, they can have free reign.

With the proliferation and widespread adoption of cloud computing solutions, HIPAA covered entities and business associates are unsure whether and how they can take advantage of cloud computing while complying with regulations protecting the privacy and security of electronic protected health information (ePHI).

Analysis of network device configurations focused on security hardening of the individual devices relative to Unatek security best practices

There are a lot of different ways that penetration testing is described, conducted and marketed. Often confused with conducting a “vulnerability scan”, “compliance audit” or “security assessment”, penetration testing stands apart from these efforts in a few critical ways:
A penetration test doesn’t stop at simply uncovering vulnerabilities: it goes the next step to actively exploit those vulnerabilities in order to prove (or disprove) real-world attack vectors against an organization’s IT assets, data, humans, and/or physical security.

Probability of HIPAA audits is increasing as the Office for Civil Rights (OCR) continues to police HIPAA violations aggressively. Data breach has become a rampant problem in the healthcare industry and in order to prevent an audit, practices must address their potential issues under HIPAA.
Pagination
- Previous page
- Page 2